Pentesting and Penetration Testing:
Everything you need to know about pen testing.
It is becoming increasingly important for companies and organizations to have pen testing performed on their (web) application, website, IT infrastructure, interfaces (APIs) and/or mobile apps. A penetration test (also known as a pen test) can reveal where the risks and vulnerabilities of the systems under investigation lie. In addition, improvements can be targeted to strengthen security to mitigate risks and vulnerabilities.
What exactly is a pen test?
A pen test, or penetration test or penetration testing, is an important element within IT and organizational security. It is basically an authorized simulated attack on a computer system, carried out to evaluate vulnerabilities. Pen testing often involves the use of a penetration testing toolkit. This toolkit contains various tools and techniques that help expose any weaknesses. The user, in this case the organization, uses the results of the pen test to get a better picture of the current security status.
Thus, an effective security audit can be conducted to target security gaps. That’s why pen tests are so important; they provide insight into vulnerabilities that might otherwise be overlooked.
A pen test at NFIR is performed by certified ethical hackers who examine your systems for vulnerabilities. The ethical hackers try to uncover weaknesses in systems in various ways. Through a combination of automated tooling and creativity, ethical hackers attempt to gain unauthorized access to information and/or systems. A pen test is always commissioned and authorized by the owners of the systems being tested. In fact, if there is no indemnification statement then there is computer infringement. After a pen test is performed, the findings are shared with the client through a report. This report describes in detail the vulnerabilities found, determines the scores using the CVSS (Common Vulnerability Scoring System) and provides advice on how to fix the vulnerabilities. It is recommended that a pen test be performed periodically, as a pen test is a snapshot in time and environments are often subject to change.
Curious about a sample report from a Pentest?
The pentest
How does a pentest work?
Pentesting helps with a crucial task for IT and security teams within any organization. It is a technique used to identify vulnerabilities in a network for the purpose of proving the vulnerabilities. By performing pen testing, organizations can proactively address potential problems and risks before they are exploited by malicious parties. Pentests use several tools to examine various aspects of a network, such as application behavior and the effectiveness of security measures. Thus, by understanding the basics of pen testing, organizations can make the best use of their resources to strengthen their security. Therefore, it is also crucial for organizations to conduct a thorough pen test by a certified party.
How does a pentest work?
The process of a pentest at NFIR begins with an intake meeting with the client. In this conversation, the research area, or scope, is determined together and the most effective approach is advised. It is essential to clearly define the objectives and exact scope of the pentest. After this conversation, NFIR prepares a detailed quote that includes the job description, the chosen pen testing method, the expected timeframe and cost. This quote also includes the contact information for the NFIR team. If there is potential contact with personal data during the pentest, it is necessary for the client to offer a processor agreement to NFIR in advance.
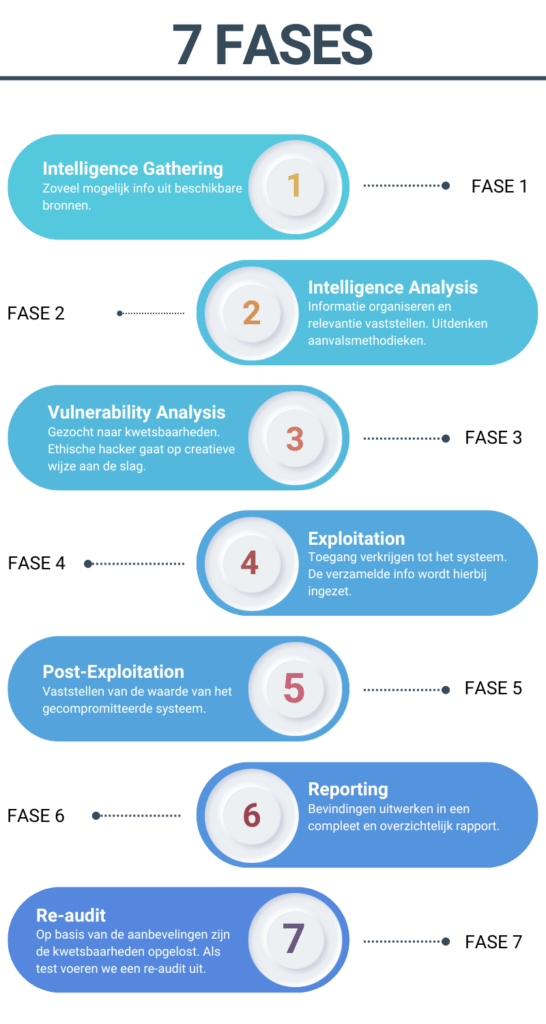
The 7 phases of a penetration test
After the quote and indemnification statement are signed, the pen test will be scheduled in consultation with the client. Penetration testing is a structured process designed to evaluate the security of systems and applications. This process is carried out in seven successive stages. The phases range from gathering information to reassessing security after implementing recommendations. These stages provide a thorough and systematic assessment of potential vulnerabilities.
Your pen testing in stages
Pen tests go through specific phases. The seven phases during a penetration test are:
- Phase 1: Intelligence Gathering
- Phase 2: Intelligence Analysis
- Phase 3: Vulnerability analysis
- Phase 4: Exploitation
- Phase 5: Post-Exploitation.
- Phase 6: Reporting
- Phase 7: Re-Audit
From pen testing to clear reporting!
Step 1: intake
During the intake, we discuss the scope components and attack scenarios of the pen test. An ethical hacker from NFIR is also present during the intake.
The intake is an important starting point because we would like to test all components within the scope of the pen test and identify all vulnerabilities. Based on the intake, we provide an hourly estimate and proposal.
Step 2: Proposal and agreements
After you receive the hour estimate and proposal, we will be happy to discuss your questions.
In consultation, we will find a suitable time to perform the pen test.
Step 3. implementation
During the pen test, we keep you informed about progress and vulnerabilities.
Critical vulnerabilities are reported immediately so that they can be resolved as soon as possible.
Step 4: Results
The vulnerabilities are documented in a clear and complete pen testing report. A standard part of our pentest services is to explain the findings following the delivered pentest report.
This explanation is greatly appreciated by our clients.
Step 5: Perfecting
Thanks to the clear insights, you are going to mitigate the vulnerabilities.
If required, we can arrange for a retest after the vulnerabilities have been mitigated. Based on this retest, you will receive a new pen test report and have confirmation that the vulnerabilities have actually been fixed
Let us assess your risks!
Find out how safe you really are and contact us today.
The scope of the test
Before confirming the assignment, the scope of the pen test must be clear. Determining the scope of the pen test is crucial to a successful security audit. The scope is the object of investigation, also known as the area of investigation. When performing a pen test, IT professionals take a meticulous approach to identifying vulnerabilities in your organization. By defining the scope, or scope, of the pentest, it is possible to determine which systems and networks will be examined. Depending on the type of pen test, no, limited or complete information about the scope will be shared by the client with NFIR. This helps identify potential risks and threats specific to your organization.
Types of penetration tests
There are different types of attack scenarios in pen testing.
Each attack scenario has its unique focus and methodology. The purpose of pen testing is to evaluate an organization’s IT security and identify potential system vulnerabilities. It may take several days to complete a pentest, depending on the scope. A certified ethical hacker is used to perform the pen test. These ethical hackers use their skills to test system security and discover any vulnerabilities. Pen testing makes it possible to test an organization’s security measures and then improve them. The ultimate goal, of course, is to prevent future cyberattacks.
To identify technical security risks or misuse of an IT infrastructure, website, (mobile) application or link(s), there are roughly three types of pentests that can be performed. The different types of attack scenarios that may be considered during the pen test are the Black Box, Grey Box and White Box. The attack scenarios are explained below.
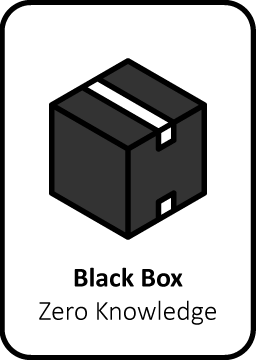
Black Box pentest
A Black Box audit can be compared to a real attack, like hackers would do. No information has been provided by the client in advance. Our ethical hackers will use open source research (OSINT) to map out your environment. So they can look for vulnerabilities.
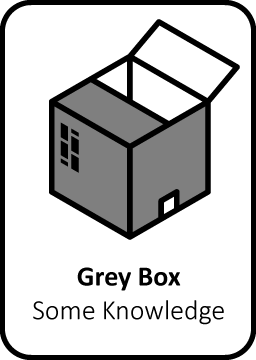
Grey Box Pentest
In this pentest, ethical hackers identify vulnerabilities in your (web) application, website, IT infrastructure, API links and mobile apps, both with and without information.
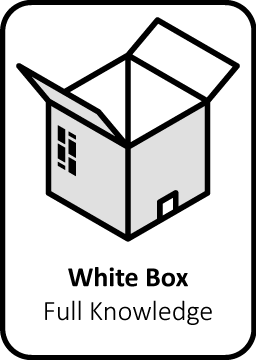
White Box Pentest
(a.k.a. Crystal box). During a White Box audit, all information is provided in advance in order to specifically search for vulnerabilities. Think of source code, defined scope, roles/rights matrix and functionalities list.
The testing methodologies of a pentest explained
When performing a pentest, it is crucial to use the right testing methodology to ensure the optimal level of security within your IT infrastructure. While each organization is unique in terms of hardware and network, all professional pen testing follows a standardized process that largely consists of identifying, analyzing and exploiting potential vulnerabilities. An ethical hacker approaches infrastructure from the point of view of a potential attacker. It is important to carefully select both the scope of the pentest and the specific type of pentest to ensure that all possible attack vectors are considered. Regardless of the testing method chosen, it’s all about optimizing your organization’s security.
To perform a successful pen test, NFIR uses several methods for information security testing. The three most important standards (depending on the environment being tested) are the Penetration Execution Standard (PTES) and the 2 standards of the organization Open Web Application Security Project (OWASP). The standards are; The WSTG and the MASTG. The Common Vulnerability Scoring System version 4.0, abbreviated to the CVSS risk model, is used to determine the severity of a vulnerability. This international model is used by NFIR to classify security breaches.
Why and when do you conduct a pentest?
There are several reasons to perform a pentest in your IT organization. The primary goal of pen testing is to gain an understanding of the strength of your organization’s security infrastructure against possible hacker attacks. Pentesting helps organizations identify vulnerabilities (also known as “vulnerabilities”) in their networks, systems or applications. These can then be addressed before a malicious hacker can exploit them. Pentests also give organizations a better understanding of how a hacker might attempt to circumvent security. We recommend performing pen tests periodically, not only after major infrastructure changes, but also as a security review to proactively protect your organization.
As such, the results of the pen test are best viewed as a snapshot in time.
Since 25 May 2018, the General Data Protection Regulation (AVG) has entered into force, which stipulates that personal data must be protected against leaks and misuse. By taking appropriate technical and organizational measures, personal data can be protected. A pentest is one of these appropriate measures because it provides insight into the risks and vulnerabilities of the environments investigated. It also checks whether (company) sensitive information is properly secured. Based on the advice from a pentest, risks and vulnerabilities can be mitigated and an organisation can take its security to a higher level. Having a pentest carried out is a valuable assessment of the systems examined, in which a report discusses the risks and vulnerabilities identified in a report and suggests possible recommendations for improvement.
Looking for more information about pen testing?
NFIR employs specialists who know everything there is to know about pen testing and carefully uncover vulnerabilities. Would you like to know what we can do for you with our pentests? Then contact us! We perform pentests on your (web) application, website, IT infrastructure, links (APIs) and mobile apps and can review code from your software if required.
Discover Our Pentest Services!
Do you need a thorough pen test for your application, website, IT infrastructure or mobile apps?
NFIR’s experts carefully uncover vulnerabilities.
Contact us directly to see how we can help you!
Pentesting is essential for any organization. They provide insight into vulnerabilities within your platform or workplace that could potentially be exploited by malicious parties. Incidents such as hacking often expose these vulnerabilities. By proactively performing pen testing, these vulnerabilities can be identified and addressed before they pose a real danger. Regular pentests contribute to a more robust security of your organization and reduce the likelihood of successful cyber attacks. This makes your business a safer place to operate. An important reference point in identifying these vulnerabilities is the Common Vulnerability Exposures (CVE) database, which provides detailed information about vulnerabilities in computer systems and networks. Many penetration test reports refer to this database. Also check out the latest Threat Intelligence reports from NFIR.
What is the difference between a pentest and a vulnerability scan
-
A vulnerability scan uses automated scans to discover known vulnerabilities. These vulnerabilities are then reported. It is an important first step in understanding potential weaknesses within a system.
A pen test goes one step further. During a pentest, not only are vulnerabilities identified, but they are actually exploited. This demonstrates what the actual consequence may be to a system or environment when compromised. The ethical hacker will use his experience and creativity to identify all the weaknesses of an environment, giving the organization a more realistic picture of the risks they face.
What methods do you use to perform pentests?
When performing a pentest, various international standards and methodologies are used to discover and classify vulnerabilities. Some of the key standards applicable to the assignment include:
- Penetration Testing Execution Standard (PTES): methodology for the purpose of infrastructure pen testing.
- OWASP WSTG: Standard for the purpose of Web application pentesting.
- OWASP Top 10: The 10 most critical web application vulnerabilities.
- OWASP API Security Top 10: The 10 most critical API vulnerabilities.
- OWASP MASTG: Standard for the purpose of mobile application pentesting.
- Common Vulnerability Scoring System (CVSS): Used to classify the severity of vulnerabilities.
By using these standards, a pentest can be performed in a structured and thorough manner, and the results can be reported in a clear and comparable way.
The Penetration Testing Execution Standard (PTES).
The Penetration Testing Execution Standard (PTES) consists of several main components. These cover everything about a penetration test, namely:
- The initial communication and reasoning behind a pentest;
- The information gathering and threat modelling phases, where testers work behind the scenes to gain a better understanding of the tested organisation;
- Vulnerability assessment, exploitation and post-exploitation, which addresses the technical security expertise of the testers and combines it with the business insight of the assignment;
- Reporting, which captures the entire process in a way that makes sense to the customer and provides them with the most value.
OWASP WSTG
The Web Security Testing Guide (WSTG) project is the premier cybersecurity testing resource for Web application developers and security professionals. The WSTG is a comprehensive guide to testing the security of Web applications and Web services. Created through the combined efforts of cybersecurity professionals and dedicated volunteers, the WSTG provides a framework of best practices used by penetration testers and organizations around the world.
OWASP MASTG
The OWASP Mobile Application Security Testing guide is a mobile app security standard and comprehensive testing guide that covers the processes, techniques and tools used during a mobile app security test, as well as a comprehensive set of test cases that allow testers to deliver consistent and complete results.
Common Vulnerability Scoring System (CVSS).
The Common Vulnerability Scoring System (CVSS) standard provides an open framework for disclosing the characteristics and consequences of software and hardware security vulnerabilities. The quantitative model is designed to ensure consistent and accurate measurement while allowing users to see the underlying vulnerability characteristics used to generate the scores.
What is the Common Vulnerability Scoring System (CVSS 4.0)
CVSS is an industry standard for assessing the severity of security vulnerabilities in computer systems. It provides scores based on various metrics to determine the impact and exploitability of vulnerabilities. Scores range from 0 to 10, with 10 being the most severe. CVSS consists of three sets of metrics: Base Metrics (inherent vulnerability), Temporal Metrics (evolution of vulnerability) and Environmental Metrics (context of vulnerability). These scores help prioritize responses to vulnerabilities.
- CVSS is an industry standard for assessing computer security vulnerabilities.
- It assigns scores based on Base Metrics (inherent vulnerability), Temporal Metrics (evolution of vulnerability) and Environmental Metrics (context of vulnerability).
- Scores range from 0 to 10, with 10 indicating the most severe vulnerability.
- CVSS helps prioritize security responses and resources.
- It includes metrics such as access capabilities, attack complexity, authentication requirements and impact on confidentiality, integrity and data availability.
- CVSS version 3 (CVSS v3) was introduced in June 2015 to address some shortcomings in previous versions.
- CVSS v3 introduced new metrics such as User Interaction and Privileges Required to assess security vulnerabilities in more detail.
How long does a pentest take?
Depending on the size of the job, a careful assessment is made as to whether multiple people should be put on a pentest to reduce the length of the job. The duration of a pentest can vary depending on the environment being tested and the complexity of the attack scenarios being used. Generally, a pentest covers a period of 2 to 4 weeks. This period includes not only the execution of the test itself, but also the preparation, analysis and explanation of the final report.
Black box or white box scenario?
When choosing the right pentest platform, it is important to consider some important aspects. First, the platform must be able to identify vulnerabilities in your IT systems. In addition, the platform should provide tools to help your organization mitigate these vulnerabilities. The security functionalities of the platform are also crucial. It should allow for both “white box” and “black box” pen testing. Selecting the right pentest platform can help you maintain a better security posture and enable your IT and security teams to work more effectively. Is your organization already doing pen testing, or are you still looking for more information about pen testing? Remember, an informed choice can be critical to your organization’s security.
- A Black Box pentest means that no information about the environment is shared with the pen testers beforehand.
- With a pentest based on the White Box principle, all information about the environment is shared in advance.
- If you are having a pentest performed for the first time and want to get an overall picture of your security, it is useful to have a Black Box pen test performed.
What more does a grey-box pentest offer than a black-box?
- A Black Box pentest is especially suitable when an environment is being pen tested for the first time and you want to get an overall picture of the security.
- A Grey Box Penetration Test is an intermediate form of the Black Box and White Box Penetration Test, in which the researchers have limited login details and information at their disposal.
- The Grey Box pentest is generally used to see how safe an environment is from the perspective of an employee or customer.
Make good arrangements about the pentest
When it comes to IT security, there are some crucial questions you should be asking. Why? Because it helps identify potential vulnerabilities, and leads to effective security measures. A factor here is that “pentesting,” or penetration testing, is a crucial part of ethical hacking. It is not just a matter of ticking boxes, but a process that can take several days. A carefully conducted pen test can discover unauthorized access to your IT systems and expose these vulnerabilities. So choose the right pentest partner NFIR and maintain control of your security. Look beyond IT, because pen testing is also about overall corporate security!
Make good arrangements about the pentest
- Make arrangements with each other when the information should be delivered, when the pentest will take place, what the pen test means for the daily operations within your company and when the report will be delivered.
- The assignment must be clear and the information required in advance must be provided on time, otherwise a pentest cannot start.
Penetration tests by our certified experts
NFIR B.V. is known as your expert in pen testing and IT security. We understand that every organization is unique and therefore have a personalized approach for each IT environment. With our expertise, we identify vulnerabilities within your network and help your organization secure itself. Whether it is a simple pentest or a complex penetration test, NFIR strives to ensure the security of your network. Our pen testing services combine both security and IT knowledge to perform the most effective tests. We understand that your IT environment is an essential part of your organization’s functioning, so we strive to protect it from potential cyber attacks. NFIR is your trusted partner in pen testing and IT security.
Certified and quality-focused Ethical Hackers
Our skilled and professional ethical hackers have extensive experience, creativity and up-to-date professional knowledge. They have completed relevant training and are certified, such as:
In addition NFIR holds a CCV seal of approval for pen testing.
Are you dealing with a security incident? How NFIR helps
If you are dealing with a security incident, you can rely on NFIR’s expertise. We offer a unique approach to finding IT vulnerabilities. Our ethical hackers are well trained and work according to standardized ISO norms to find vulnerabilities in your IT.
Whether you have a vulnerability in your infrastructure, need insight into threat vectors or need an ethical hacker to understand how attackers can penetrate, NFIR can help. We perform detailed pen testing that delivers an accurate and understandable report. This provides you with a clear picture of your current security and offers concrete recommendations for improvement. Moreover, you can expect results within days, which means you can take quick action to strengthen your IT security. NFIR’s help significantly reduces the risk of hacking.
High quality pen testing
Certified and quality-oriented pentesters
Pentests are essential to test the technical resilience and effective operation of security. Our pentesters focus on identifying vulnerabilities in systems by deploying various attack techniques. Our skilled and professional pen testers have extensive experience, creativity and up-to-date professional knowledge. The pentesters have completed various relevant training courses and hold the following certifications, among others, OSCP, OSWP, OSWE, OSEP, CPTS, CBBH, and eWPT.
Pentesting and the CCV seal of approval:
- This quality mark, based on NEN-EN-ISO/IEC standards 17021 and 17065, gives customers the guarantee that the execution of a pen testing assignment by NFIR is carried out in a professional and high-quality manner.
- NFIR possesses since 07-01-2022 the CCV quality mark for Pentesting.
I want to pentest my environment(s)!
- Once you fill out this form, we will contact you immediately to inform you of the possibilities.
- We schedule a no-obligation intake with a Technical Lead to coordinate scope components and attack scenarios.
"*" indicates required fields

Certified pentesters
The team consists of certified and experienced Technical Leads and pentesters. Specializing in various environments.
Professional approach
Committed Technical Leads and Project Coordinators ensure high-quality pen testing according to the CCV quality mark.

Extensive experience
Have a pen test performed by a team that performs hundreds of pen tests annually with an average customer satisfaction rating of 8.4

Clear and transparent
The pen test report is clear, complete and actionable. We always provide an explanation and are also available to you after the project.